wgc operations push command.
This not only saves bandwidth but can also help reduce the attack surface by allowing only safe-listed operations.
Architecture
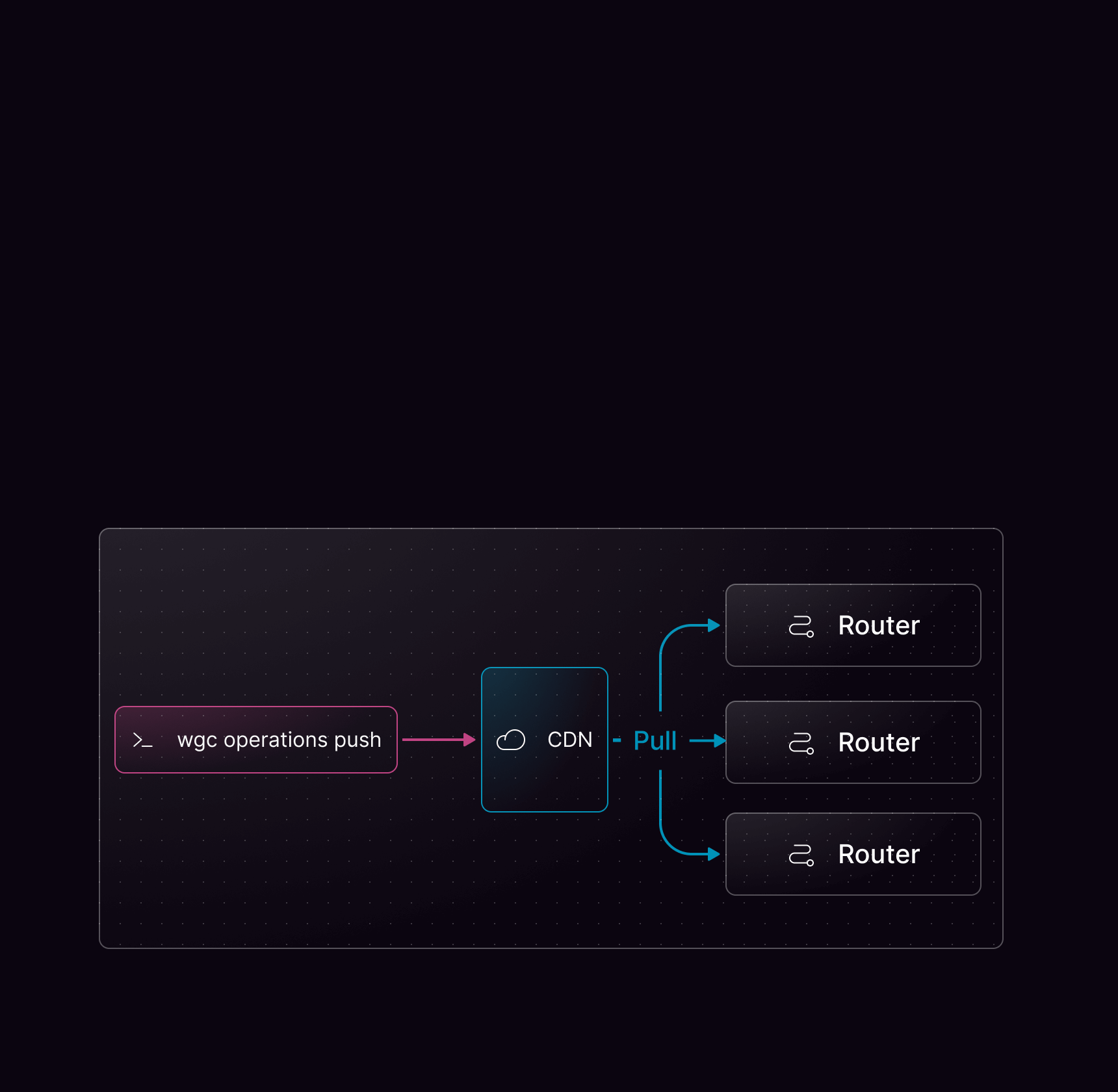
Using persisted operations
Persisted operations require some tooling on the client side. Consult the documentation for your GraphQL client library to find out how to generate a query manifest or query map. Once this list of operations has been generated, typically in your CI or CD pipeline, you can usewgc to register your operations:
mygraph in the default namespace (as seen in the Studio) and your client named web (indicated by the graphql-client-name HTTP header), using the same operation identifiers as your library when possible. If your library doesn’t generate these identifiers, Cosmo will automatically generate them.
When pushing the operations, you will see a short summary of the operations that were pushed, indicating how many were created and how many were already registered. Alternatively, the --output flag can be used to obtain a JSON summary that can easily be processed by your tooling.
wgc operations push, see Push.
Additionally, check the Using Persisted Operation with Federated GraphQL tutorial for a step-by-step guide.
Deleting persisted operations in Studio
You can delete persisted operations directly in Cosmo Studio after they have been uploaded viawgc operations push.
- Open your federated graph in Studio.
- Go to Clients.
- Open a client and click View Operations.
- Expand the operation and click the delete button.
- Confirm in the delete dialog.
organization-admin or organization-developer roles can delete operations.
Operations are currently deleted one at a time from the UI.
Studio always asks for confirmation before deleting operations. If traffic is detected for the selected operation, the dialog warns that the operation is receiving traffic. If analytics data is unavailable, Studio cannot guarantee that existing clients won’t break. You can always check the metrics using the link in the dialog.
Disallowing non-persisted Operations
If you’re going all in on Security, you’d want to only allow Persisted Operations in your Production Environment. By default, non-persisted (dynamic) GraphQL Operations are allowed, which you can disable using the Security Configuration of the Router. We expose 4 different types of persisted operation blocking in the configuration:- Allow all operations (Default) — Both persisted and dynamic operations are permitted.
- Log unknown operations — Any operation that has not been persisted will be logged, but not blocked.
- Safelist — Operations that have been explicitly persisted will be allowed, based on matching the query body against persisted queries.
- Block non-persisted operations — Fully enforced blocking of non-persisted operations, clients are required to send a pre-computed SHA-256 hash instead of a query body.
Migration path to enforcing persisted operations
To migrate from allowing all operations to a more restrictive option incrementally, we recommend following these steps:Enable log_unknown
This will log when clients use operations that have not been persisted, helping you identify which operations to persist.
Enable safelist
This will allow users to send operations with any query body, but only execute if they match a persisted operation.
Important Considerations
-
Whitespace sensitivity Differences in whitespace can alter an operations hash, which will cause it to be rejected as an unknown operation. We recommend using
log_unknown_operationsbefore enabling full blocking. -
Compatibility with Automatic Persisted Queries (APQ) The
safelistoption cannot be used alongside APQ, as their functions are opposite.